Default role
The default role applies to all new members. You may change the default role to any one of the predefined or custom roles to match your requirements.
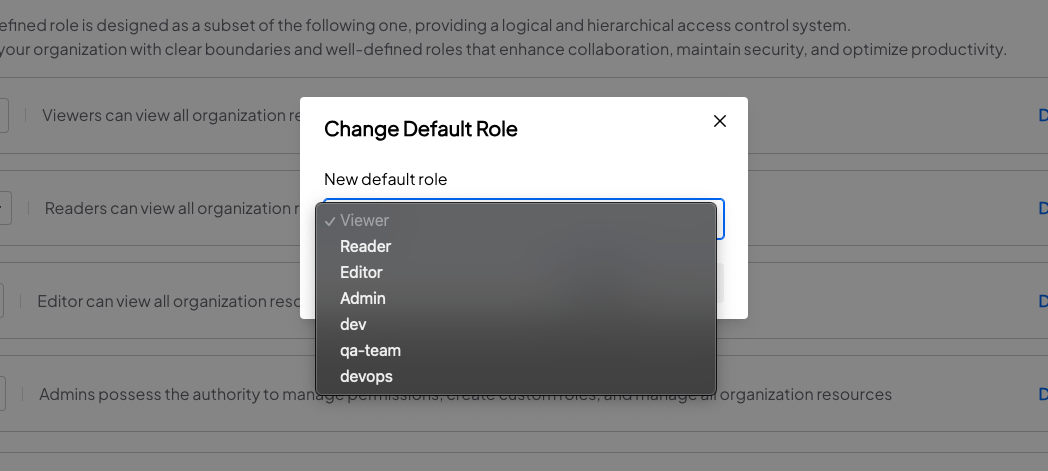
Changing the default role does not change the roles of existing members.
Tokens receive a default role of
reader and are not affected by the default role.Predefined roles
Each predefined role is designed as a subset of the following one, providing a logical and hierarchical access control system. Empower your organization with clear boundaries and well-defined roles that enhance collaboration, maintain security, and optimize productivity.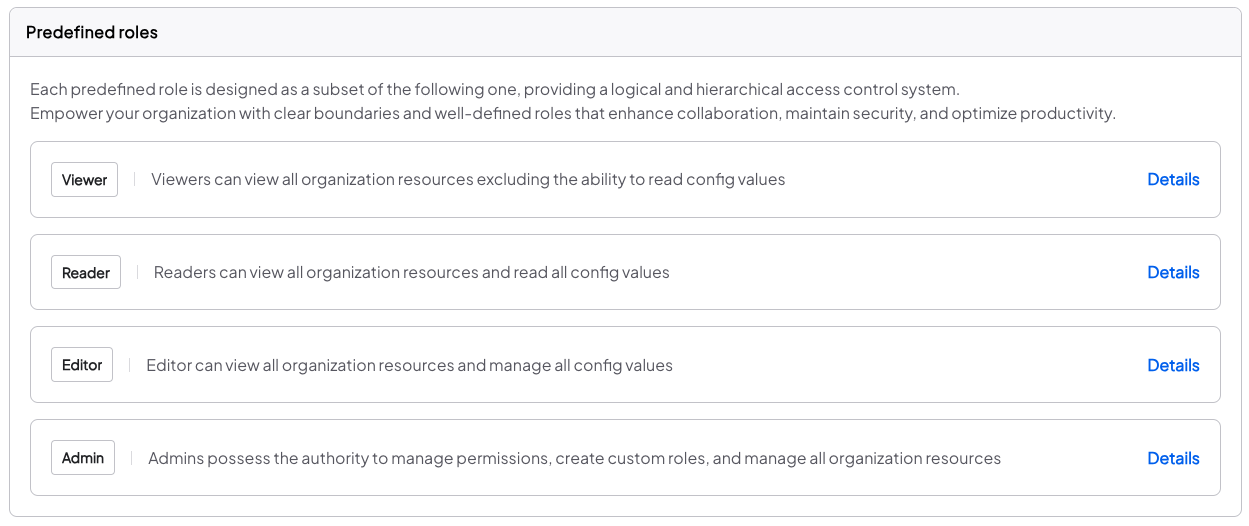
Predefined roles are immutable and cannot be changed or deleted.
The Admin role allows management of members, tokens, roles, webhooks, and organization settings.
The Admin role allows management of members, tokens, roles, webhooks, and organization settings.
Assign roles
Members and tokens can be assigned a single predefined and any amount of custom roles which give stacking permissions on top of the predefined role permissions. For example:- User “John Doe” has the “Reader” predefined role and a custom role named “Developer” that has the write permission for the “dev” config set.
- “John Doe” can:
- Read config values of all config sets due to the “Reader” role.
- Write config values to the “dev” config set and all its children due to the “Developer” Role
Creating a custom role
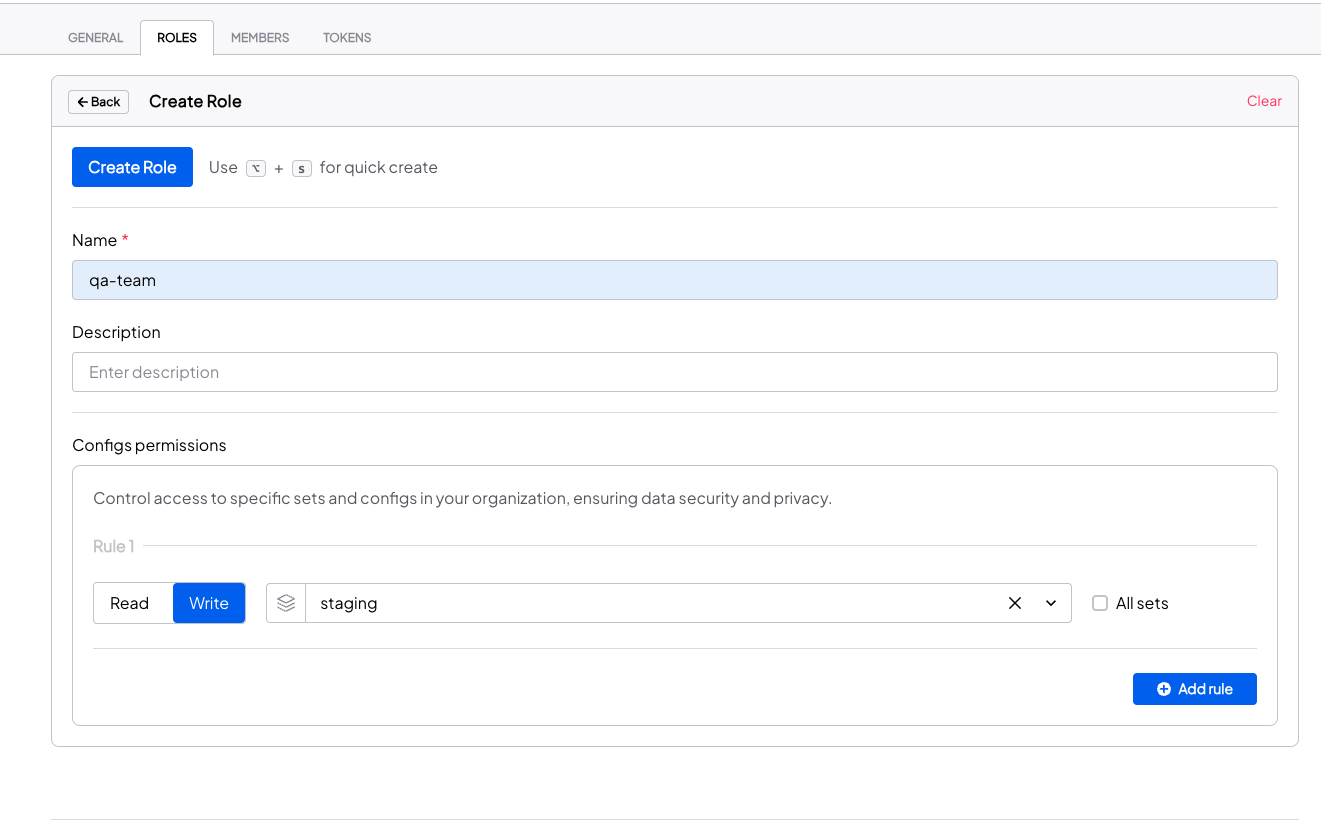
Take control of your organization’s access management with our flexible and dynamic custom roles feature. Every organization is unique, with specific requirements and workflows. That’s why we empower you to create custom roles, allowing you to fine-tune access permissions according to your exact need.- Go to the Roles page under the Settings tab.
- Click the Create Role button and provide the role name and role permissions.
- After adding the role, you will see it listed in the custom roles list.
The read permission grants access to read config values of the selected set and its parent sets.
The write permission grants access to read and edit config values of the selected set and its child sets.
The read all permission grants access to read config values of all sets.
The write all permission grants access to read and edit config values of all sets.
Duplicate rules are omitted when creating/updating roles.
The write permission grants access to read and edit config values of the selected set and its child sets.
The read all permission grants access to read config values of all sets.
The write all permission grants access to read and edit config values of all sets.
Duplicate rules are omitted when creating/updating roles.
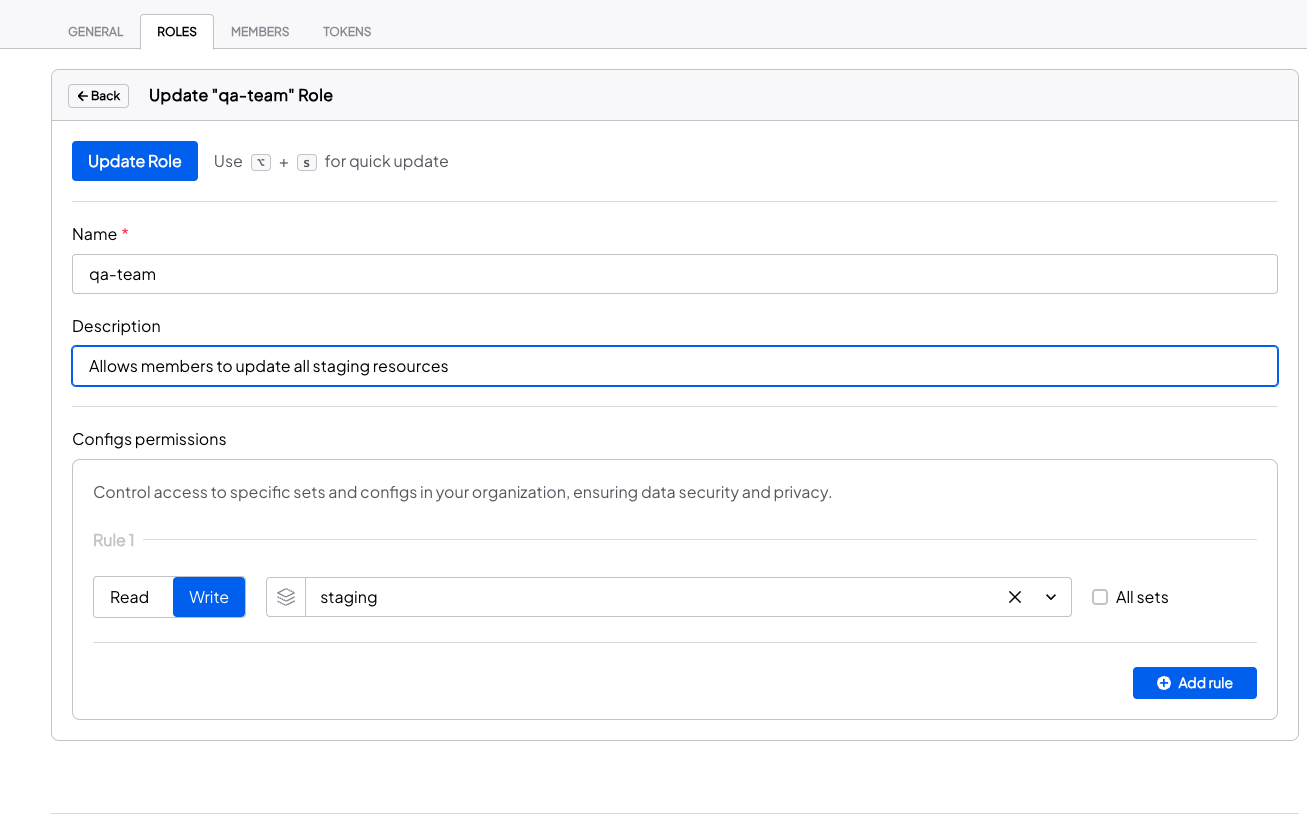
Updating a custom role
Deleting a custom role
Assign config attribute
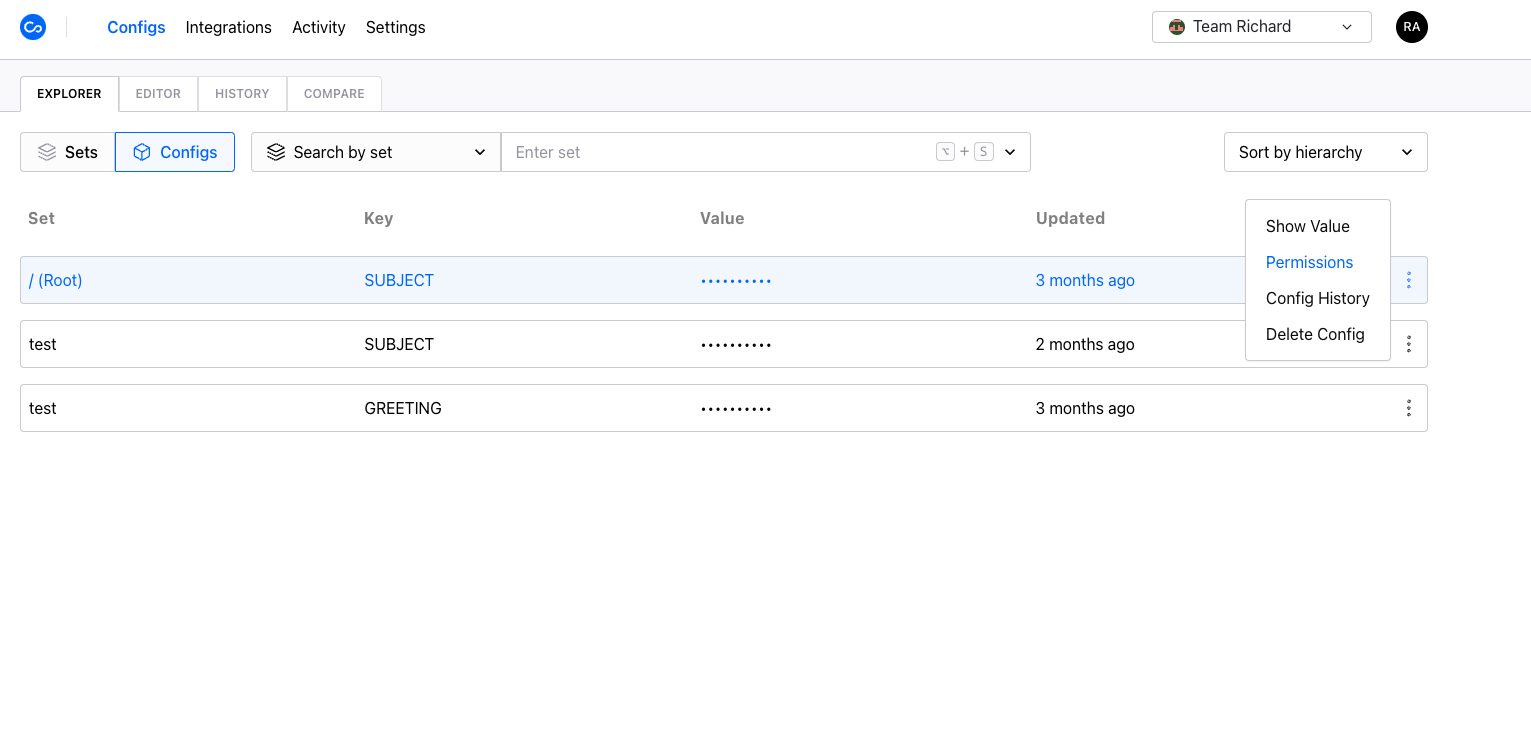
Members can be assigned a config attribute which gives them access to a specific config within a config set.- Go to the Configs page under the Explorer tab.
- Open a config’s action menu and click Permissions. Pick one or more members and assign them a desired attribute.
- After assigning an attribute, the member will be able to access the config with the granted permission.
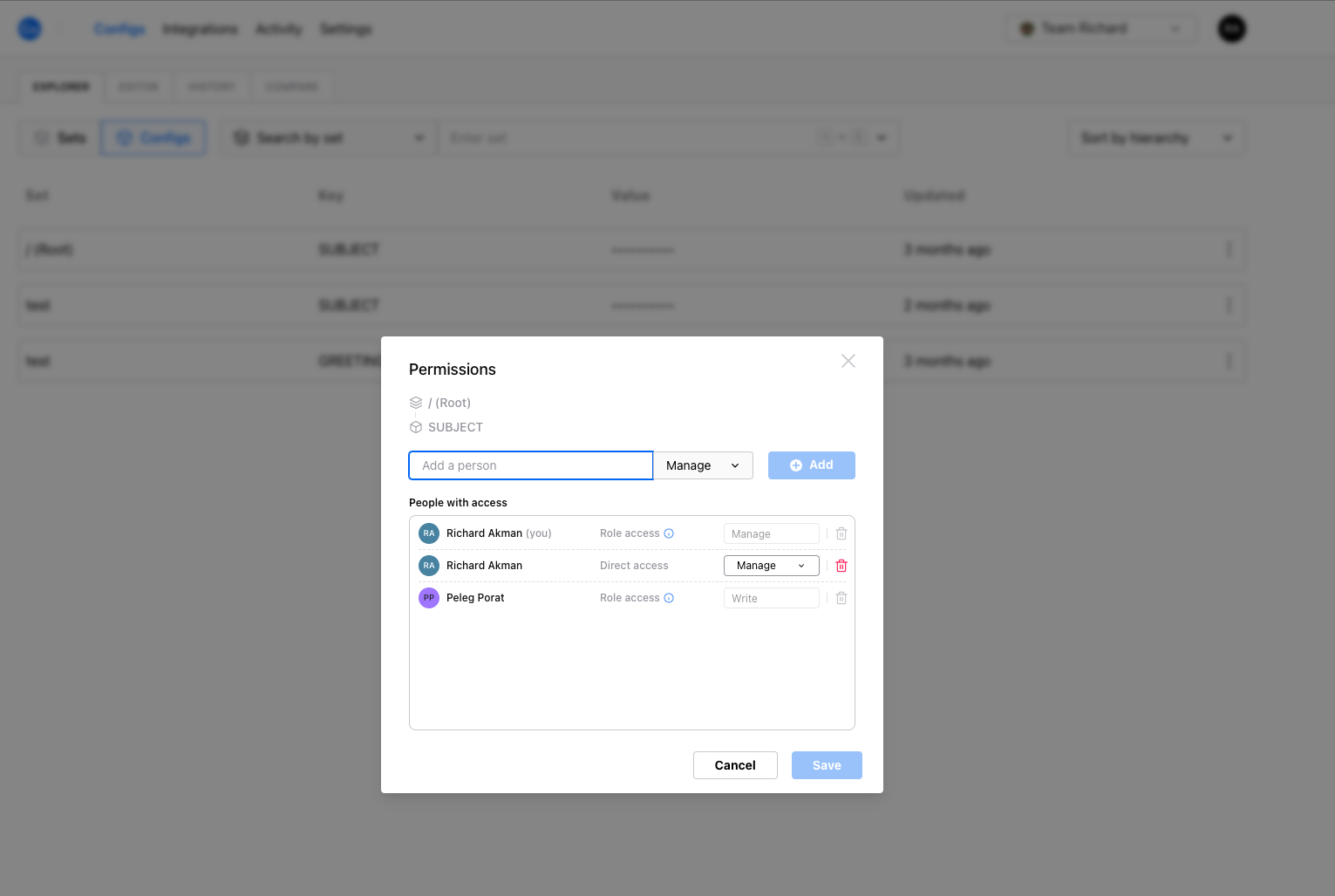
The read permission grants access to read the config value.
The write permission grants access to edit the config.
The manage permission grants access to edit the config and also assign config attributes to other members.
Tokens cannot be assigned a config attribute.
Only members with the Admin and Owner role can initially assign attributes.
Attributes are additive, meaning that a member with multiple attributes will have the union of all their permissions.
The write permission grants access to edit the config.
The manage permission grants access to edit the config and also assign config attributes to other members.
Tokens cannot be assigned a config attribute.
Only members with the Admin and Owner role can initially assign attributes.
Attributes are additive, meaning that a member with multiple attributes will have the union of all their permissions.

